Your Cart is Empty
Customer Testimonials
-
"Great customer service. The folks at Novedge were super helpful in navigating a somewhat complicated order including software upgrades and serial numbers in various stages of inactivity. They were friendly and helpful throughout the process.."
Ruben Ruckmark
"Quick & very helpful. We have been using Novedge for years and are very happy with their quick service when we need to make a purchase and excellent support resolving any issues."
Will Woodson
"Scott is the best. He reminds me about subscriptions dates, guides me in the correct direction for updates. He always responds promptly to me. He is literally the reason I continue to work with Novedge and will do so in the future."
Edward Mchugh
"Calvin Lok is “the man”. After my purchase of Sketchup 2021, he called me and provided step-by-step instructions to ease me through difficulties I was having with the setup of my new software."
Mike Borzage
Standards-Based APIs for a Continuous Digital Thread: OPC UA, REST, gRPC for Model-Centric Design-to-Factory Integration
November 05, 2025 14 min read
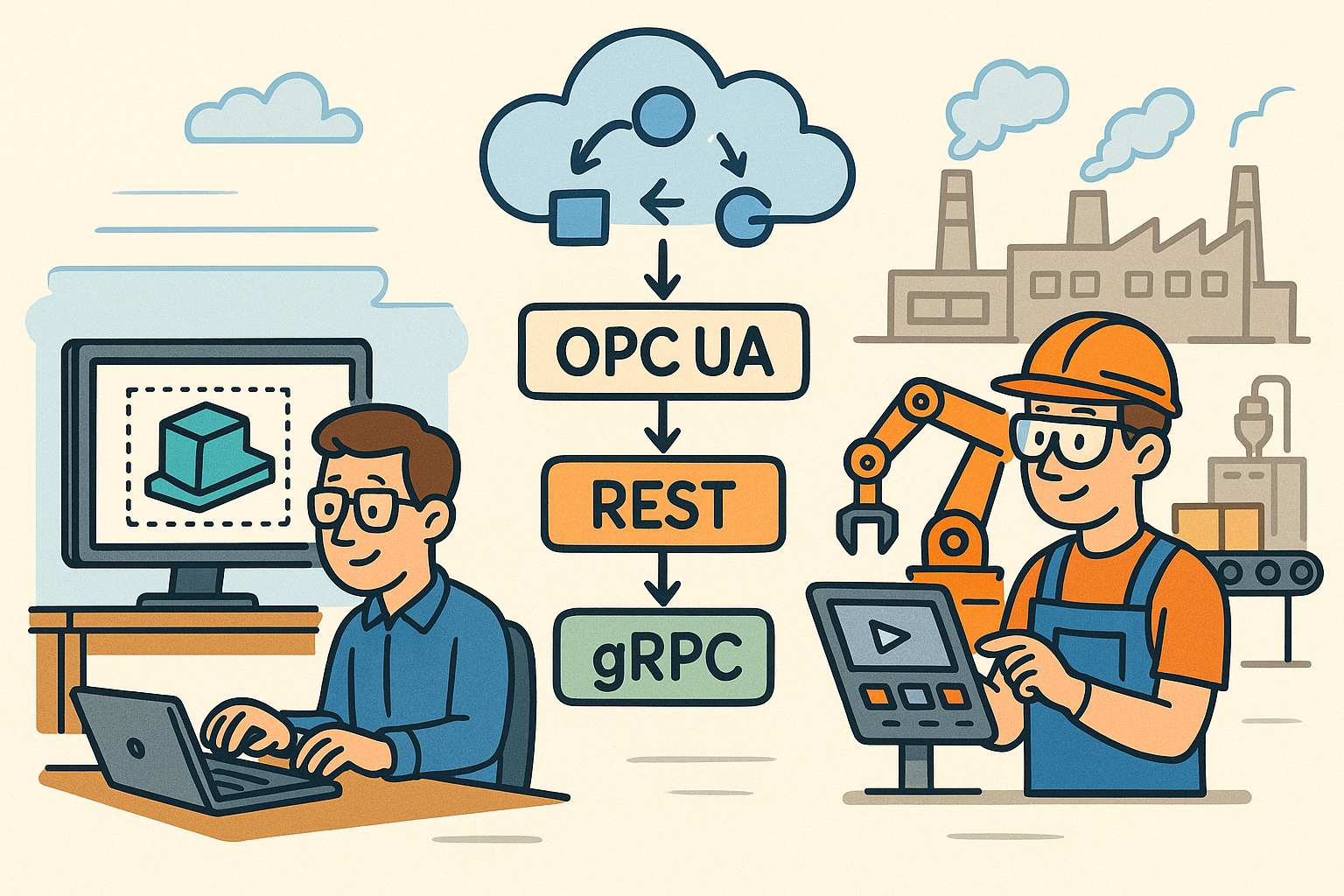

Introduction
The past decade compressed the distance between design studios, engineering offices, and factory floors into seconds. Yet many organizations still shuttle files and spreadsheets through air gaps that fracture context, lose intent, and create rework. The fix is neither another monolith nor a proprietary connector web. It is a disciplined adoption of **standards-based APIs** that bridge **CAD/PLM**, **MES/SCADA/PLC**, and analytics ecosystems into a **continuous digital thread**. In practice, this means aligning semantics, not just moving bytes; matching protocols to intent, not fashion; and treating security, observability, and failure as first-class design concerns. This article offers a pragmatic blueprint: why the approach matters to business outcomes; reference architectures that survive real factories; a detailed implementation playbook with contracts, data models, and example flows; and the guardrails that keep integrations resilient. By the end, you will have the language, structures, and patterns to connect model-centric design, governed transactions, and real-time control—without surrendering performance or compliance. The emphasis is on **OPC UA** for equipment semantics and control, **REST** for governed CRUD and transactions, and **gRPC** for low-latency streaming and microservice pipelines, all underpinned by shared identifiers and models such as **ISA‑95**, **OPC UA Companion Specifications**, and **STEP/AP242**. Minimal ceremony, maximal clarity, and durable interoperability guide every recommendation that follows.
Why standards-based APIs across design and factory matter
Business outcomes
Standards-based APIs align the decisions made in design with the actions executed in production, allowing organizations to operate a verifiable, closed-loop system rather than a patchwork of brittle connections. When **CAD/PLM decisions** flow to **MES/SCADA/PLC** execution via governed contracts, every change inherits traceability from the outset: which design revision spawned which NC program, which tool offsets were applied, which lot and serial numbers were affected, and what in-situ measurements corroborated conformance. This unlocks measurable outcomes in operational excellence and regulatory compliance. Engineering change lead time shrinks because validation, instruction generation, and dispatch are automated through machine-readable semantics instead of email threads. Meanwhile, quality improves when process signatures and **in-situ monitoring** flow back to design to inform tolerances, materials, and manufacturability rules. Organizations benefit from fewer defects, faster ramp to rate, and a richer corpus of production knowledge that can be mined for optimization. Crucially, these benefits accrue across supply chains: suppliers can subscribe to controlled updates and publish back as-built evidence in harmonized formats, enabling shared KPIs without shared infrastructure. The result is a **continuous digital thread** that is both observable and governable, where deviations trigger immediate containment and long-term design improvements rather than postmortems. This is not integration for integration’s sake—it is integration that compounds over time.
- Connect design intent to execution reliably, not best-effort file drops.
- Automate traceability for regulated contexts and high-mix environments.
- Feed process and quality signals back to design for true closed-loop engineering.
Interoperability challenges
Interoperability fails most often on semantics and timing, not transport. Real factories operate on **heterogeneous vendor stacks**, long-lived **legacy controllers**, and proprietary data tags accreted over years. Even when connectivity exists, **semantic mismatches** between product structures—such as multi-level BOMs, **MBD/PMI** annotations, and configuration rules—and shop-floor constructs—such as routes, work centers, fixtures, and tool lists—introduce ambiguity. A product’s “revision” is not the same as a program’s “version,” and a fixture’s identity may be conflated with a cell’s. The **time scales diverge** as well: PLM and ERP are transactional and governance-heavy, while PLCs and motion controllers operate on millisecond control cycles. If these domains are bridged naïvely, systems either throttle production with transactional overhead or leak control semantics into business systems. Finally, terminology drift—units, tolerance conventions, and state machines—causes subtle defects: a temperature reported in Fahrenheit enters a rule expecting Celsius, or a “complete” work order masks an outstanding inspection step. Solving these problems demands consistent information models, canonical identifiers, and well-chosen protocols that respect the constraints of each layer while providing a shared vocabulary across them.
- Heterogeneous stacks: controllers, robots, HMIs, historians, and gateways with divergent tag schemas.
- Product vs. process semantics: BOM/MBOM, PMI vs. routes/resources cause misalignment.
- Timing mismatch: transactional governance vs. real-time control loops.
Choosing the right protocol for the job
Protocols encode design intent as much as payload bytes do. **OPC UA** brings an information model with types, methods, events, and a browseable address space—a natural fit for **equipment semantics and control**. It supports subscriptions, historical access, and a robust security model, which map well to production cells and lines. **REST** shines for **governed CRUD** and transactional operations—parts, revisions, work orders, NC programs—where idempotence, cacheability, and mature API governance are critical. OpenAPI documents provide shared contracts, and gateways enforce authN/authZ and quotas. **gRPC** excels for **low-latency** microservices and **bi-directional streaming**, ideal for telemetry enrichment, anomaly detection, simulation, and optimization pipelines. It pairs with Protobuf to minimize bandwidth and CPU overhead and aligns tightly with polyglot microservices. Choosing “the one protocol” is a trap; the winning pattern is protocol polyglot with clear boundaries: OPC UA at the equipment edge, REST for master data and business transactions, and gRPC for analytics and streaming services. This separation avoids using REST for high-frequency data or overloading OPC UA with opaque tag dumps. It also enables independent scaling, QoS, and governance suited to each domain.
- OPC UA: industrial semantics, subscriptions, methods, secure channels.
- REST: cacheable CRUD, strong governance, idempotent commands.
- gRPC: streaming, Protobuf efficiency, microservice-friendly.
Semantic alignment prerequisites
Before the first line of code, invest in shared semantics. Adopt **ISA‑95/ISA‑88** for enterprise, site, area, line, and cell hierarchies, and for batch and procedural models. Use **OPC UA Companion Specifications** (e.g., Machinery, Robotics, CNC) to standardize nodesets and method signatures. Represent model-based definition with **STEP/AP242** so PMI and GD&T carry through to process planning and metrology. Embrace the **Asset Administration Shell (AAS)** to structure digital twins of assets, enabling discoverable submodels for identification, documentation, and condition. Establish a **shared identifier strategy**: how part numbers map to revisions and configurations; how work orders map to operations, cells, fixtures, and program versions; how serials and lots propagate through assembly. Decide unit systems and **tolerance conventions** up front, with canonical units (SI preferred) and explicit conversions at boundaries. These agreements are not bureaucratic overhead; they are the substrate for reliable automation, analytics, and compliance. With semantics aligned, streams and transactions become composable, and correlation across **PLM, MES, and equipment** becomes routine rather than heroic effort.
- Adopt ISA‑95/88, OPC UA Companion Specs, AAS, and STEP/AP242.
- Define durable IDs and correlation keys spanning PLM, MES, and shop-floor assets.
- Standardize units and tolerances; enforce conversions at system boundaries.
Reference architectures and integration patterns
Edge-to-cloud bridge
The canonical pattern starts at the cell. An **OPC UA client** discovers and subscribes to nodes across PLCs, robots, and CNCs, reading parameters, state, and in-situ measurements while writing bounded setpoints and invoking methods under safety interlocks. An **edge normalizer** enriches these signals with metadata: asset identities (AAS), process context (work order, operation, program revision), and unit conversions. Telemetry flows out via **OPC UA PubSub over MQTT/AMQP** or is transformed into **gRPC/Protobuf** streams for analytics and feature extraction. At the same edge, a **REST facade** exposes device inventory, configuration, and job status for governance and orchestration. This three-protocol braid isolates concerns: real-time control and semantics stay within OPC UA; managed transactions and configuration live in REST; and high-rate telemetry leverages gRPC or PubSub to backpressure and scale independently. Store-and-forward buffers absorb network partitions, while a thin policy engine enforces limits and rollback. The cloud side ingests streams into durable backbones (Kafka/MQTT), persists time series in specialized stores, and surfaces contracts to PLM/MES via REST, enabling a unified but decoupled system.
- OPC UA client/bridge in the cell; edge metadata enrichment and unit normalization.
- Telemetry via UA PubSub→MQTT/AMQP or UA→gRPC translation for analytics.
- REST at the edge for inventory, configuration, and job orchestration.
Event-driven digital thread
Events stitch the digital thread without conflating streams and commands. **CAD/PLM emits design and revision events** whenever parts, PMI, or NC programs change. **MES subscribes**, validates, and materializes work instructions and routes tied explicitly to the design revision. Throughout execution, correlation IDs bind work orders, as-planned steps, and as-built lots/serials, carrying forward into inspections and deviations. Telemetry—temperatures, spindle loads, acoustic emissions—flows in high-rate streams, while commands—start job, update parameter, pause cell—arrive as **idempotent REST** calls or **OPC UA method** invocations. This separation prevents the common anti-pattern of treating streams as commands or vice versa. Downstream analytics detect anomalies and publish **nonconformance events**, which in turn open PLM change tasks with evidence links to time series segments, images, and logs. Event schemas evolve under versioned contracts, and consumers opt-in to additive fields. This architecture sustains scale and change by decoupling producers and consumers across domains while preserving traceability end to end.
- Design events drive materialization of work instructions and routes in MES.
- Correlation IDs unify as-designed, as-planned, and as-built records.
- Streams for telemetry; commands via idempotent REST or OPC UA methods.
Security and governance
In a connected factory, every interface is a potential attack surface. Adopt a **zero‑trust** posture from edge to cloud. Enforce mTLS everywhere: **OPC UA SecureChannel**, **gRPC TLS**, and **REST with OAuth2/OIDC** access tokens. Certificates are per device/agent with short lifetimes and automated rotation. Authorization is **attribute-based (ABAC)**, scoping access by asset, cell, role, and purpose; privileges are least-privilege and time-bound. Every action produces an **immutable audit log** with actor, subject, intent, and correlation ID. Data governance differentiates stream types: telemetry, which is high volume and ephemeral; and traceability records, which require long retention and hashing for integrity. Residency policies account for jurisdictional constraints, particularly for multi-region suppliers. API gateways, OPC UA reverse proxies, and service meshes provide policy enforcement, rate limiting, and DDoS protection. Finally, governance includes API lifecycle: consumer onboarding, test environments with synthetic devices, schema registries, and conformance test suites. Security is not a bolt-on; it is the scaffolding that makes the digital thread safe to operate at scale.
- mTLS, short-lived certs, and automated rotation across all protocols.
- ABAC tied to asset, cell, and role; immutable audit logs.
- Data residency and retention policies per stream and record type.
Reliability and performance
Manufacturing tolerates downtime poorly and unpredictability even less. Build reliability by design. At the edge, **store‑and‑forward buffers** insulate against WAN disruptions; backpressure and **rate limiting** protect downstream systems from floods. Commands are **idempotent** and carry **deduplication keys**; events deliver at least once with sequence numbers and consumer-side idempotency to avoid double-processing. For determinism, maintain **clock sync** using PTP/NTP with monotonic fallbacks and include timestamps, sequence numbers, and QoS indicators in your payloads. Protocol encoding matters: **OPC UA binary** is efficient for control and tightly constrained environments; JSON improves readability but costs CPU and bandwidth; **Protobuf** for gRPC blends compactness with strong typing; compression should have thresholds to avoid wasting cycles on small messages. Always budget latency end-to-end: from change events in PLM to parameter updates at the cell, and from sensor to decision to actuation. SLOs—such as “99th percentile closed-loop adjustment within 2 seconds”—guide design choices and capacity plans.
- Edge buffers, backpressure, and rate limits to tame variability.
- Idempotent commands, dedupe keys, and at-least-once events with sequence numbers.
- Clock sync and QoS profiles for deterministic behavior; encoding trade-offs explicit.
Protocol bridging cautions
Bridging protocols without preserving meaning is a fast route to haunted integrations. When mapping **OPC UA nodes** to **REST** or **gRPC** contracts, ensure that the source semantics—units, engineering ranges, state machines, and method preconditions—propagate into the target model. Do not flatten rich hierarchies into anonymous “tag dumps”; define typed resources and messages that mirror the domain. Avoid using REST for high-frequency streams; it leads to broken caches, overloaded gateways, and poor observability. Likewise, refrain from cramming transactional updates into opaque OPC UA tags; use methods with explicit signatures and error codes. Bridges must also manage timing: if a REST transaction commits, but the downstream OPC UA method fails, implement compensating actions and transactional outboxes rather than best-effort retries. Finally, version both ends. When OPC UA nodesets evolve, reflect changes in REST/gRPC contracts through additive fields and deprecation windows, not silent rewrites. Bridging is a translation task; treat it with the rigor of language translation—syntax, vocabulary, and context all matter.
- Preserve units, ranges, and state semantics across mappings.
- Keep REST for transactions, gRPC/UA PubSub for streams, UA methods for control.
- Version bridges and contracts; avoid opaque “tag jungles.”
Implementation playbook with concrete flows
Contract-first interfaces
Begin with contracts, not code. For **REST**, publish **OpenAPI** specs that define explicit resources—parts, revisions, work orders, NC programs, quality records—with schemas, validation, and examples. Model actions as state transitions and idempotent commands (e.g., POST /work-orders/{id}:start) with clear error semantics. For **gRPC**, design **Protobuf** messages for telemetry, anomaly events, and simulation/optimization jobs, including well-defined envelopes that carry correlation IDs, timestamps, and QoS metadata. For **OPC UA**, design **nodesets** with standard types and adopt **Companion Specifications** wherever possible so method names, event types, and variable nodes match industry conventions. Apply a **versioning strategy** across all interfaces: SemVer with additive changes preferred, explicit deprecation windows, changelogs, and automated lints that block breaking changes without an opt-in migration path. Treat contracts as your most critical asset: store them in version control, review them like code, test them with consumer-driven contract tests, and publish them in a developer portal with examples and SDKs. The contract-first approach reduces ambiguity, accelerates onboarding, and sustains compatibility over years.
- REST via OpenAPI; explicit resources and idempotent command endpoints.
- gRPC with Protobuf schemas for streams and compute jobs.
- OPC UA nodesets aligned to Companion Specs; documented methods and events.
- SemVer, additive evolution, and deprecation policies enforced by lints.
Data model bridging
Even perfect APIs fail if identifiers and units drift. Create an **ID registry** that maps **part numbers and revisions (PLM)** to **operations, cells, fixtures, and programs (MES/SCADA)** with globally unique, immutable identifiers. Embed those IDs in OPC UA node metadata and gRPC envelopes so context travels with signals. Promote **units and tolerances** from MBD PMI into process specifications: a hole position tolerance becomes a fixture capability requirement and a metrology plan characteristic. Enforce **canonical units** (SI) at the edge and convert at visualization layers. Curate **quality features** by defining characteristic IDs that link SPC charts, metrology device outputs, and **CAD GD&T** annotations; ensure evidence (images, point clouds, time series) references the same IDs and revisions. Document state machines for parts, operations, and equipment with allowed transitions and error states; reflect these in both REST resources and OPC UA variables. The result is traceability that is algorithmically reliable: joins across systems no longer depend on fuzzy keys or naming conventions but on deliberate, typed identifiers that survive renaming and migration.
- Global ID registry connecting PLM parts/revisions with MES operations/cells/fixtures.
- Canonical units and tolerance propagation from PMI to process and inspection.
- Characteristic IDs unify SPC, metrology, and CAD annotations.
Example end-to-end flows
Ground the architecture with disciplined flows that test contracts and semantics under realistic timing and failure scenarios. In a **Design change → CAM → MES** flow, a PLM revision event triggers automated CAM validation against machine capabilities and cutting rules; results post back via REST, and approved NC programs are dispatched to cells through **OPC UA methods** with safety checks and human-in-the-loop approvals where required. For **In‑situ monitoring → deviation to design**, OPC UA telemetry streams through an edge gateway to **gRPC** analytics; anomalies generate **nonconformance records** and open PLM change tasks with links to signal segments and images, preserving evidence. In **Runtime parameter optimization**, MES issues parameter updates via REST to the edge controller, which applies **bounded setpoints** through OPC UA under interlocks; rollbacks occur automatically if control loop stability or quality KPI thresholds are breached. Each flow uses correlation IDs from design revision to as-built lot and captures timing metrics. Idempotent commands avoid double-starts, and compensating actions handle partial failures, ensuring the system remains auditable and resilient.
- Design→CAM→MES: PLM event, CAM validation, REST results, OPC UA program dispatch.
- In-situ monitoring→Deviation: UA→gRPC analytics, anomaly→PLM change with evidence links.
- Runtime optimization: REST orchestration, UA setpoints with safety interlocks and rollback.
Tooling and operations
Select tools that operationalize the contracts. For OPC UA, libraries such as **open62541** and **UA-.NETStandard** accelerate client/server development and conformance. For REST↔gRPC interoperability, use **grpc-gateway** or **Envoy** to expose HTTP/JSON surfaces while maintaining internal Protobuf streams. Adopt **API gateways** for auth, quotas, and transformation. For data, establish **Kafka** or **MQTT** as event backbones, **TimescaleDB** or **InfluxDB** for time series, and object stores for heavy evidence (point clouds, images, logs). Testing must be industrial-grade: run **PLC/robot simulators**, **OPC UA conformance tests**, and **contract testing** (e.g., Pact) to keep producers and consumers aligned. Practice **chaos drills** that sever links while validating store-and-forward, backpressure, and alerting. For observability, standardize on **OpenTelemetry** tracing across REST/gRPC, and collect OPC UA session metrics (subscriptions, queue depths, reconnects). Define SLOs for **E2E latency** and **data completeness** per flow, and wire them to dashboards and alerts. Tooling is not a footnote; it is the difference between a demo and a production system that survives maintenance windows and WAN flaps.
- SDKs: open62541, UA-.NETStandard; grpc-gateway, Envoy; managed API gateways.
- Data systems: Kafka/MQTT, Timescale/InfluxDB, object stores for evidence.
- Testing: simulators, OPC UA conformance, contract tests, chaos drills.
- Observability: OpenTelemetry, OPC UA metrics, SLOs for latency and completeness.
Anti-patterns to avoid
Several traps repeatedly sink integrations. Avoid the **mega‑API** temptation: one endpoint surface that blends master data, transactions, telemetry, and control. It yields unclear SLAs, runaway coupling, and security sprawl. Do not build **custom tag jungles**; modeling everything as arbitrary strings sabotages discoverability, validation, and analytics. Resist the urge to skip **edge buffering**; networks fail and need mitigation, not hope. Never ignore **backward compatibility**; breaking changes ripple across suppliers and lines, causing unplanned downtime and expensive coordination. Do not misapply protocols: REST is not a streaming substrate; OPC UA is not a dumping ground for opaque JSON blobs. Finally, treat observability and security as features, not chores; systems without tracing, metrics, and strong auth devolve into pager fatigue and compliance headaches. Naming these anti-patterns early helps teams design review checklists and automated guardrails that prevent them from slipping into roadmaps under deadline pressure.
- No “one API to rule them all”; separate transactional and streaming concerns.
- No custom tag jungles; use standard information models.
- No assumptions of perfect networks; edge buffers and retries are mandatory.
- No breaking changes without versioning and deprecation paths.
Conclusion
Key takeaways
Durable interoperability in manufacturing emerges from deliberate choices. Match **protocol to intent**: use **OPC UA** for **equipment semantics and control**, **REST** for governed transactions and master data, and **gRPC** for high-performance streaming and microservices. Prioritize **semantics over transport** by investing in shared models—**ISA‑95/88**, **OPC UA Companion Specs**, **AAS**, **STEP/AP242**—and in a robust identifier and correlation strategy. Engineer for **security, observability, and failure** from day one: zero-trust mTLS, ABAC, immutable audit logs, OpenTelemetry traces, and edge store‑and‑forward buffers. Anchor all of this in contract-first interfaces with versioning discipline, and validate with testable flows that exercise the full path from **as-designed** to **as-built** and back to **as‑planned** improvements. The payoff is a **continuous digital thread** that compresses engineering cycles, elevates quality, and scales across suppliers without surrendering control or compliance.
- OPC UA for equipment, REST for transactions, gRPC for streaming and analytics.
- Semantics and IDs are the bedrock; transport is the vehicle.
- Design for security, observability, and failure as requirements, not afterthoughts.
Phased roadmap
Start small, prove value, and scale with governance. Phase one pilots a single cell with an **edge bridge** that speaks OPC UA and exposes REST and gRPC per contract-first specs. Use synthetic workloads and simulators to validate reliability and SLOs before touching production. Phase two scales to lines and plants: standardize **nodesets**, introduce an **event backbone** (Kafka/MQTT), and expand the ID registry to encompass fixtures and metrology. Roll out automated conformance tests and schema registries, and migrate manual dispatch to API-driven orchestration with human-in-the-loop approvals. Phase three institutionalizes governance: establish an **API lifecycle** with review boards, semantic versioning policies, consumer-driven contract tests, and observability standards. Extend the digital thread to suppliers via curated, least-privilege portals and tokens. At each phase, sunset bespoke connectors, capture metrics, and feed lessons into playbooks and templates. This cadence makes progress tangible while avoiding big-bang risk, allowing teams to learn with guardrails and to scale with confidence.
- Pilot a cell with OPC UA edge bridge and contract-first APIs.
- Scale to lines/plants with event backbones and standardized nodesets.
- Institutionalize governance: lifecycle, schema registry, conformance tests.
Success metrics
Measure outcomes, not activity. Track **engineering change (ECN) to first‑article lead time** and set aggressive but realistic improvement targets. Monitor the **percentage of lots with full as‑designed↔as‑built traceability**, verifying that correlation IDs flow from PLM through MES to equipment and quality systems. Enforce and observe an **end‑to‑end latency budget** for closed-loop adjustments—sensor to decision to actuation within defined targets at the 95th and 99th percentiles. Finally, instrument the integration fabric to report the **mean time to diagnose** faults using traces and logs; aim for minutes, not hours. Complement these with system health SLOs: event loss rates, buffer utilization, subscription churn, and API error budgets. When these metrics trend in the right direction, the digital thread is not just built—it is operating as a living, resilient system that improves design, accelerates production, and sustains compliance at scale.
- Reduced ECN-to-first-article lead time.
- Higher share of lots with end-to-end traceability completeness.
- Closed-loop latency within SLOs for adjustments.
- Rapid diagnosis of faults via traces and logs (reduced MTTD/MTTR).
Also in Design News

Cinema 4D Tip: Filmic OCIO Pipeline and Camera-Based Exposure
November 05, 2025 2 min read
Read More
Bluebeam Tip: Track accountability with the Owner field in Bluebeam Revu
November 05, 2025 2 min read
Read More
ZBrush Tip: IMM workflow for distortion‑free inserts and fast curve placement
November 05, 2025 2 min read
Read MoreSubscribe
Sign up to get the latest on sales, new releases and more …


